SECURITY REVELATIONS: Messages between Chinese hackers show Australian Strategic Policy Institute is a target
Chinese spies have identified an Australian research institute as a priority target in their cyber-attack operations, with The Nightly able to confirm messages about our nation. WARNING: COARSE LANGUAGE

WARNING: COARSE LANGUAGE
Chinese spymasters have identified Australia’s top security research institute as a priority target in their cyber-attack operations, with an investigation by The Nightly for the first time able to reveal messages between hackers that refer to our nation.
The group chat exchanges also offer a remarkable insight into the daily lives and frustrations of state-sponsored hackers working for China, including their dismay at being told they’re working too slowly while being tasked with disrupting “a big asset in two days”.
Sign up to The Nightly's newsletters.
Get the first look at the digital newspaper, curated daily stories and breaking headlines delivered to your inbox.
By continuing you agree to our Terms and Privacy Policy.The Nightly investigation can reveal hackers working for the Chinese Government have been directed to target the Australian Strategic Policy Institute.
Withdrawing funding for the institute was among 14 demands to the Australian Government released by the Chinese embassy in 2020.
Among its other grievances was “thinly veiled allegations against China on cyber attacks without any evidence” and a rebuke of the Australian government it repeated as recently as last fortnight when a Chinese Foreign Ministry spokesperson said “China firmly opposes and combats all kinds of cyber attacks”.
But The Nightly has discovered group chat messages on a social media channel exchanged between a hacker collective working for the Chinese Government.
The messages reveal a target list that includes ASPI — a think tank partly funded by Australia’s Department of Defence — among a range of other governmental organisation across the US and Taiwan.
In the exchanges, the hackers discuss hitting critical infrastructure in the Indo-Pacific, receiving directives to support Chinese security agencies and receiving letters of thanks for their service.

This is the first time a cyber offensive against Australia has been publicly attributed to written directives for intelligence activity sponsored by the Chinese Government.
It is also the first time an Australian media outlet has published Chinese national security agency directives.
The ASPI has contracts to deliver military research and training to the Department of Defence and cyber intelligence agency the Australian Signals Directorate.
The institute counts current and former senior officials from the defence and intelligence communities within its ranks.
The Nightly has independently verified that hackers in the collective appear to have compromised a power station in South Korea’s Jeollabuk-do province in September, and has reported this to the South Korean Government. The power station’s website was taken offline at the time.
Introducing the hackers in August, a leader refers to and names a spymaster, and says: “Every practical operation of our organisation is approved by the higher-ups, and it has nothing to do with the black market.
“Our financial source comes from the boss of the organisation. He’s not a hacker but a leader.”
China’s Ministry of State Security, also known as MSS, and other intelligence and military agencies engage external hackers as well as deploying their own operatives in a practice known as state-sponsored hacking.
The hacker tasked with targeting the ASPI attributed the target list to a handler from Fujian in a September message. Fujian is a south-east province in China with a diaspora concentrated in the Indo-Pacific.
“This revelation is a sad reminder that the Chinese Communist Party will try to suppress any source of legitimate criticism, at home and abroad,” ASPI executive director Justin Bassi said.
There is no suggestion that the Chinese Government or its network of state-sponsored hackers has successfully compromised the ASPI’s cyber security.
The US’ Defence Advanced Research Projects Agency, responsible for developing specialist military technologies, is also listed as a target.
As are its Army Medical Research Institute of Infectious Diseases, responsible for researching defences against biological warfare, and the Office of Chemical and Biological Weapons Affairs, a State Department initiative promoting a global ban on chemical and biological warfare.
All three US targets are listed below the ASPI, which itself sits below the Taiwan National Defence Medical Centre Institute of Preventive Medicine and the Kunyang Laboratory of the Taiwan Centres for Disease Control and Prevention.
The group chat messages, largely from the second half of last year, show Chinese cyber security professionals being cultivated and controlled by the Chinese Government to perform state-sponsored work.
They are similar to exchanges displayed by the I-Soon data leak in February, in which hundreds of conversations were leaked on open-source repository GitHub.
The New York Times called that a “rare look inside the secretive world of China’s state-backed hackers for hire”.
In a “letter of thanks” from an entity of the Cyberspace Administration of China, the Chinese Communist Party’s top cyber and censorship agency, a hacker in the collective is recognised for having “demonstrated high political awareness, strong sense of responsibility, and excellent workability, providing strong support”.
“We hereby express our sincere gratitude to your unit. We hope that your company will continue to support relevant cybersecurity work in the future and make greater contributions to the development of the country’s cyberspace security field,”it says.
The Nightly can also reveal what a directive to support Chinese security agencies looks like.
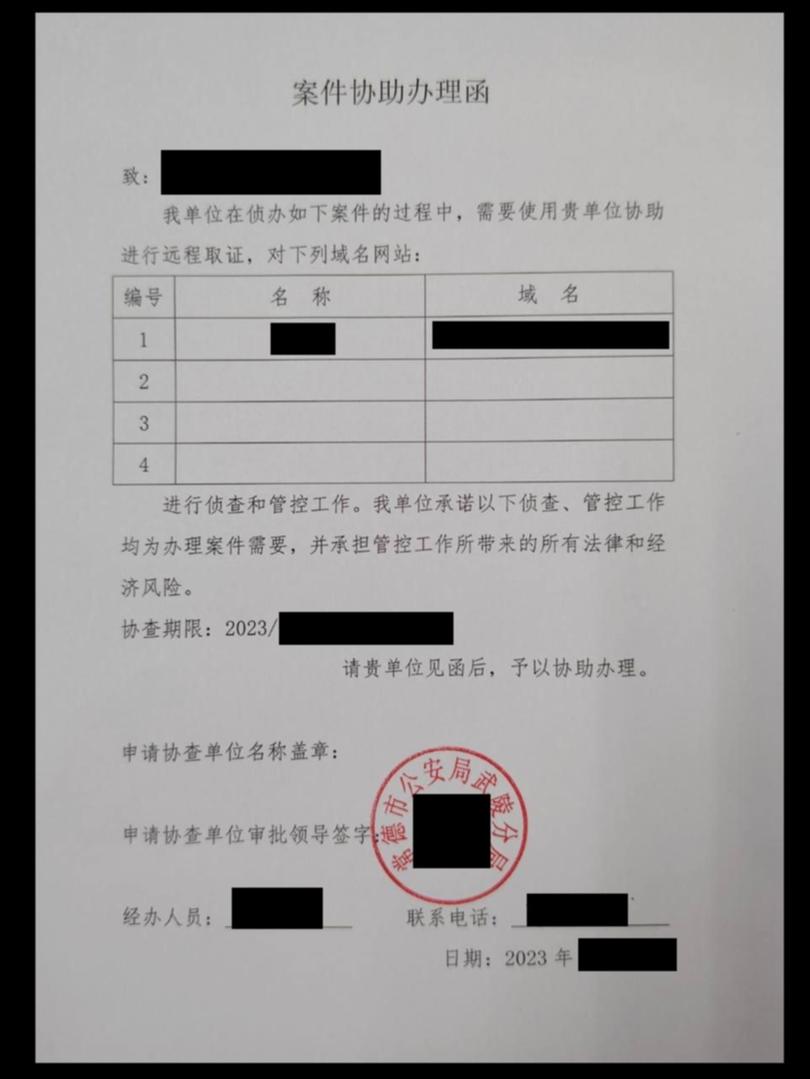
A “request for assistance” from a bureau of the Ministry of Public Security, China’s domestic national security agency, directs another hacker in the collective to: “Please assist us with the case upon receipt of this letter.”
“Our unit needs your assistance in carrying out remote evidence collection for the following case. We need to investigate and control the following domain websites,” the request from a bureau in the southern province of Hunan says.
It adds: “We hereby confirm that all investigation and control work is necessary for handling the case, and we will bear all legal and economic risks arising from the control work.”
A month after members were introduced, in September, some of the hackers express dissatisfaction with their handlers.
“I want to castrate those idiots,” one says.
Another says: “They fucking think I work too slowly, so they sent two people to ‘co-operate’ with me.”
“That motherfucker only sent it at one in the afternoon, has the nerve to say I’m fucking slow,” one says in another exchange.
Someone replies: “Leaders can toy with you, but you can’t neglect them. That’s how domestic institutions are, the main principle being it’s better for the leader to let down the world than for the world to let down the leader.”
One exasperated hacker complains: “I don’t have the ability, and I don’t know what some people are thinking, expecting me to take down such a big asset in two days.”
A peer bemoans: “Senior leaders set ambiguous and vague operational goals to indirectly set traps for those below.”
In response, the hacker tasked with attacking the ASPI, says: “Like the fucking fool from southern Fujian giving me targets without giving me any official records.”
Attached to that hacker’s message is the list of designated targets in which the ASPI appears among the US and Taiwanese targets.
The other targets are UK-headquartered international risk consultancy Control Risks, the US foreign aid Agency for International Development, Singapore-based bank Overseas-Chinese Banking Corporation and US-based private investigator network World Association of Detectives.
Chinese Government targeting of a private investigator professional association is consistent with Australian security agency warnings and international prosecutions of alleged agents of China’s Ministry of State Security.
A student member of the hacking group, who attends one of China’s top five universities, boasted that he won a university-wide cyber security vulnerability discovery competition last year.

The Nightly is not publishing their “first place” certificate as it would likely make the student identifiable.
Other student members attend Lanzhou University, Shanghai Jiao Tong University and the Beijing Institute of Technology.
All three institutions have performed joint cyber research with Australian universities.
The CSIRO, the Australian Government’s scientific research agency, performed artificial intelligence research with Shanghai Jiao Tong University last year.
“Can I tell other people about this stuff? For example, I want to ask (name redacted) for help or something. No one responded in the group, and then the so-called commander-in-chief said: Just don’t leak confidential information,” one hacker says.
Mr Bassi said the ASPI was a “national security research institute” that “identifies security threats that emanate from China and have the backing of the Chinese Government”.
“We publish those findings without fear or favour,” he said.
“That a major power is so fixated on a research institute demonstrates Beijing’s hostility towards open enquiry and debate, and it also, frankly, reflects the quality and impact of our work.
“It is important to remember that defunding the ASPI was one of the 14 demands the Chinese embassy issued Australia in 2020, along with trying to silence the free media and change legislation such as our foreign interference laws.
“I am extremely proud of the ASPI team’s research. We won’t stop doing work that is so clearly in the interests of Australia’s security and is to the benefit of open, democratic values everywhere.”
In July 2022, almost one year before Chinese spymasters designated the ASPI a target in this operation, China’s state media outlet Global Times accused it of having a “no-compromise policy” that “mirrors evil intentions to disrupt China-Australia ties”.
“It insists on creating obstacles to a better relationship with China, raising questions about whether the organisation is simply an anti-China megaphone for Washington’s strategic interests to produce public opinion ammunition against China,” the Global Times said.
The ASPI has led research into the Chinese Government’s treatment of Uyghur and other Turkic Muslim ethnic minorities in China, where Human Rights Watch believes “as many as a million people have been arbitrarily detained in 300 to 400 facilities, which include ‘political education’ camps, pretrial detention centres, and prison”.
A Department of Foreign Affairs and Trade spokesperson told The Nightly: “The Australian Government will continue to deter and respond to malicious cyber actors that threaten our national interests, including by calling out their activities when we have sufficient evidence and it is in our interests to do so.
“We have been clear in our expectation that all countries should act responsibly in cyberspace, and adhere to international law and norms.”
